Today’s review is about a pretty decent hosting company called Linode. Here’s the three-day timeline from idea to implementation:
- Thursday: decided to create a new info website about 3D printing, bought the domain name on GoDaddy and waited for the changes to take effect at midnight
- Thursday: created a Github repository to store the source for the website since I’m open-source like that
- Thursday: created an account on Linode, purchasing a “linode” for that
- Thursday: designed/created the initial local/development website layout/framework, collected images and content
- Friday: created (provisioned) the basic linode (virtual machine) for the website on production, provisioned a virtual drive, deployed Ubuntu 16.04LTS onto that, booted and remoted into that, ran updates, installed the framework, added the website, setup security and the firewall
- Friday: adjusted the DNS at GoDaddy to point to the new server, added more content
- Saturday: launched the website on Linode with the initial version
- Saturday: tweaked the settings to make the Node.js—based website start on bootup
- Saturday: added more content to the website
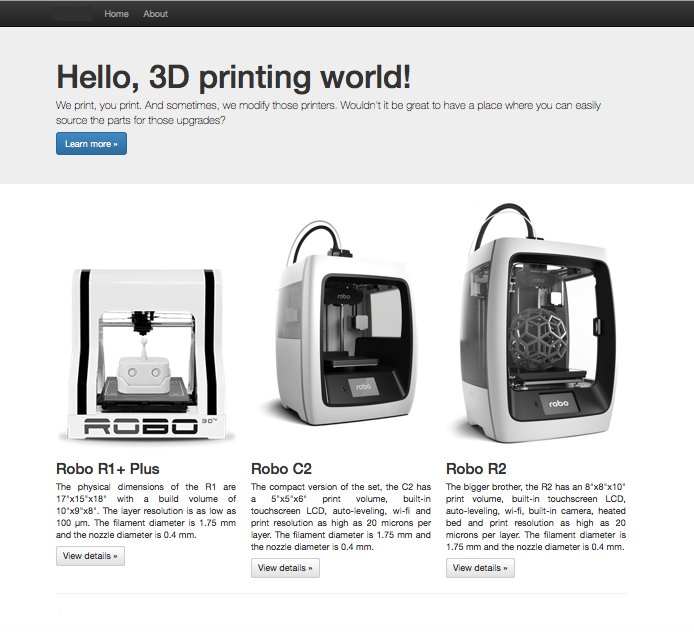
Not bad for an open-sourced 10-page (44 files) responsive website, if I do say so myself.
Please note that when I say “hosting company”, I really mean a “virtual server provider” so this is more like Amazon EC2 as a service offering. I didn’t just rent website space (like on Wix.com or WordPress.com), I rented an entire virtual server, if you will.
Comparison of virtual server versus website space
There are some advantages/disadvantages of renting a virtual server over just some website slot on a server somewhere:
Pros:
- In theory, you could run several websites from a virtual server
- You can run services in the background (like Node.js) and manage them
- You can run multiple threads on the same server, like helper routines which do something other than serving up pages
- You’re not limited to the set of templates that are available from Wix.com, for example
- Your website runs separately from other websites
- You get an IP address which is only used for your website
Cons:
- You have to setup security yourself since you’re responsible for the entire server
- The learning curve is steeper
- You have to know I.T. things like setting up servers and installing software
Framework/software
Here’s a list of what I used for this website:
- Node.js: Probably the most famous event-driven JavaScript runtime engine out there
- Express: A minimalistic Node.js framework for separating code from content on a website
- Bootstrap.css: A responsive stylesheet and component library for styling a website
- PM2: A handy process manager for Node-based applications on a server. After pulling new code, I might run the command
pm2 restart AppNameto restart the service
Documentation
Kudos to Linode for providing a detailed Getting Started guide along with several tutorial videos on the subject.
And further, a note of thanks to PM2 which seems to satisfy the requirements of bringing up and managing a Node.js application as a service within a production environment and their ample documentation.
Suitability
Is Linode well-suited for most website designers/developers? Probably not. On an I.T. complexity scale from 1 to 10 potatoes, I’d say they’re probably seven potatoes, perhaps. In this case, you’d have to be comfortable doing the following:
- Using a web-based console to allocate and bring up/down a virtual server
- Using
sshto remote into your virtual server - Navigating within a command line interface on a Linux computer or similar
- Using
ssh-keygento generate a keypair - Using
apt-getto update things - Editing files using
nano - Managing services, reading log files
- Remotely rebooting your virtual server
- Setting up a firewall, testing and managing same
- Applying code using
git - Testing a website to verify that there are no 404 (file not found) type of errors, for example
- And obviously, creating/designing a website in the first place and using a repository like Github for storing those files
That said, it was a perfect fit for me since I can do those things. In fact, the Linode-related part of this took no more than two hours since this is the first time I’ve used their interface. My next one should go much faster.
Observations
I will say that I’m impressed. Unlike Amazon AWS, Microsoft and Google, the people at Linode haven’t created an interface that’s overly complicated. It seems to work simply and to do the things you need to do and those are: 1) buy a virtual server, 2) deploy something onto it, 3) turn it on and 4) remote into it. I don’t think the “big three” have figured this out yet; their interfaces and the assumed workflow requires too much research, in my humble opinion.
Additionally, the PM2 software does a great job of working with the git-based code distribution model, allowing you to restart the Node.js app when it’s required and to start up automatically each reboot. There’s an easy-to-remember command interface like pm2 show AppName which tells you what you usually want to know.
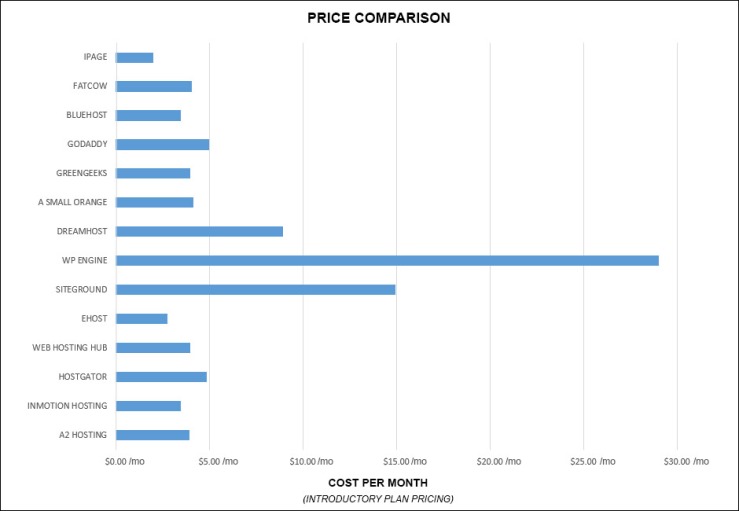
At a cost of $5/month, it compares favorably to most of the well-known hosting providers out there. The basic linode will likely satisfy the requirements of the average Node.js application up to a reasonable level of simultaneous users, I’d suggest.







 Trust
Trust
